Comptia Security+ Exam Prep 2
Quiz Summary
0 of 17 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Results
0 of 17 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
| Average score |
|
| Your score |
|
Categories
- Security+ 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- Current
- Review / Skip
- Answered
- Correct
- Incorrect
-
Question 1 of 17
1. Question
1 point(s)A company has a problem with privilege creep. Which access control model is MOST susceptible to this problem?
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 2 of 17
2. Question
1 point(s)A government agency is implementing a new security policy but decides to exempt an older, legacy system from certain requirements due to compatibility issues. What should be the agency’s primary focus to manage the risks associated with this exemption?
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 3 of 17
3. Question
1 point(s)What is the PRIMARY purpose of Security Content Automation Protocol (SCAP)?
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 4 of 17
4. Question
1 point(s)Which log entry may indicate exploitation of system vulnerabilities?
2023-04-20T08:30:00.123Z INFO ApplicationServer – User ‘jdoe’ initiated login process from IP: 172.16.254.1
2023-04-20T08:30:05.456Z INFO ApplicationServer – User ‘jdoe’ successfully authenticated.
2023-04-20T08:32:22.789Z WARN ApplicationServer – Unexpected input validation failure in module ‘PaymentProcessor’.
2023-04-20T08:33:15.012Z ERROR ApplicationServer – System exception occurred: stack overflow exception in module ‘PaymentProcessor’.
2023-04-20T08:35:00.678Z INFO ApplicationServer – New user ‘tempUser’ created by ‘admin’.
2023-04-20T08:36:45.901Z INFO ApplicationServer – User ‘tempUser’ initiated login process from IP: 203.0.113.42
2023-04-20T08:37:00.345Z INFO ApplicationServer – User ‘tempUser’ assigned role ‘Administrator’ by ‘admin’.
2023-04-20T08:39:15.678Z ALERT ApplicationServer – Multiple failed login attempts for user ‘admin’ from IP: 198.51.100.7
2023-04-20T08:41:30.123Z WARN ApplicationServer – Unusual activity: High volume of data requests by user ‘tempUser’.
2023-04-20T08:43:00.456Z ALERT ApplicationServer – Outbound traffic spike detected.
2023-04-20T08:45:30.789Z INFO ApplicationServer – User ‘jdoe’ initiated logout process.- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 5 of 17
5. Question
1 point(s)You are responsible for the security of an internal network. In reviewing the firewall rules, what potential security concern is addressed by Rule 5?
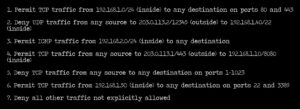
Rule 5. Deny TCP Traffic from any source to any destination on ports 1-1023
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 6 of 17
6. Question
1 point(s)A large enterprise is optimizing its network infrastructure with the implementation of load balancers. The network team is tasked with configuring the load balancers to enhance both performance and security. Which TWO of the following configurations should be applied to achieve these objectives? (SELECT TWO)
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 7 of 17
7. Question
1 point(s)An art gallery is upgrading its security systems to protect valuable artworks. The gallery is considering incorporating pressure-sensitive technologies for enhanced security. Which TWO of the following applications of pressure-sensitive technology would be most effective in securing the artworks? (SELECT TWO)
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 8 of 17
8. Question
1 point(s)Paul wants to protect sensitive data from unauthorized access and ensure that it remains confidential while being processed. Which cryptographic concept should Paul apply for this purpose?
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 9 of 17
9. Question
1 point(s)A healthcare organization handles a variety of data, including human-readable patient records and non-human-readable diagnostic machine outputs. To enhance data security, which TWO of the following measures should the organization prioritize? (SELECT TWO)
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 10 of 17
10. Question
1 point(s)A healthcare organization adheres to the principle of least privilege in managing access to patient records. However, during an internal audit, it is discovered that several administrative staff members have access to all patient records, regardless of their specific job requirements. What is the MOST likely cause of this violation of the least privilege principle?
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 11 of 17
11. Question
1 point(s)An employee receives an email from what appears to be the company’s CEO, urgently requesting the transfer of funds to a new account for a confidential deal. The email address is similar to the CEO’s but with a minor difference. What should be the employee’s response to this potential social engineering attack?
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 12 of 17
12. Question
1 point(s)A cybersecurity team in a medium-sized enterprise has automated its patch management process to enhance security. However, during the last update cycle, several critical systems experienced downtime due to incompatible patches. What is the MOST likely cause of this issue, considering the automated patch management system?
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 13 of 17
13. Question
1 point(s)During a routine security assessment, it is found that an external attacker is able to perform on-path attacks on a company’s wireless network, intercepting and altering data. Which of the following vulnerabilities is MOST likely enabling this attack?
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 14 of 17
14. Question
1 point(s)A healthcare organization is reviewing its authentication protocols to secure access to electronic health records (EHR) systems and other sensitive medical databases. The organization aims to protect patient data and ensure compliance with health data protection regulations. Which TWO of the following authentication protocols should be prioritized for implementation to achieve these objectives? (SELECT TWO)
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 15 of 17
15. Question
1 point(s)An online retailer has noticed a pattern of fraudulent transactions originating from certain IP addresses. To effectively monitor and identify such activities in the future, which detective control should the security team focus on implementing?
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 16 of 17
16. Question
1 point(s)A security team at DataSight Solutions utilizes OSINT to enhance their threat intelligence capabilities. They gather information from various online sources, including social media, forums, and news sites. To effectively use OSINT in their vulnerability management strategy, which TWO of the following actions should the team prioritize? (SELECT TWO)
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect -
Question 17 of 17
17. Question
1 point(s)A technology firm plans to implement a new secure access policy for its data center. The policy includes various authentication methods to ensure that only authorized personnel can access sensitive areas. Which TWO of the following authentication methods should the firm consider implementing to authenticate individuals effectively and enhance security? (SELECT TWO)
- 1.
- 2.
- 3.
- 4.
CorrectIncorrect